How to Protect Your WordPress Website from DDoS Attacks

Online security is a job on its own, and, in large corporations, there are specialized IT professionals who take care of all of its important aspects. However, even if you are a one-man show running a personal blog, there are steps you can take to improve your website’s security.
In this article, we will be showing you how to safeguard your WordPress website from DDoS attacks. But let us take a step back: what are WordPress DDoS attacks, and how can they harm your website? We will answer these questions before we get to the how-to.
Here’s what we’ll be discussing:
DDoS stands for Distributed Denial of Service. It is an advanced form of DoS, or denial of service attack: a form of attack whose purpose is to disrupt the normal traffic of a website, server, service, or network.
DDoS is distributed by virtue of the attack being carried out by a network of devices (a botnet) a bad actor uses in order to perform the action. The fact that an attack is distributed across a network makes it harder to detect and block.
The attack itself works by overwhelming the capacity of a server: as it struggles to handle the flood of requests, it slows up or crashes, unable to service them all.
Firstly, it makes your website run slow or crashes it. This is a very real and distinct adverse effect on your visitors’ user experience and your traffic. If you are running an online store, you may end up losing sales, while if you are hosting content, your visitors will go elsewhere to get it.
Secondly, you can lose your reputation with search engines and customers. A website which can’t be reached when needed will be shunned by potential return visitors, while SEO metrics such as authority, trust and relevance can also be affected.
Finally, it can cost you to undo the damage done, especially if you need to hire support staff or invest in a cybersecurity solution.

There are plenty of reasons why you may become a target of a WordPress DDoS attack. For instance, some bad actors may subject your website to a DDoS attack in hopes of extracting money from you in order to make the attack stop.
Or, you may be hosting content somebody finds politically controversial to the point that they will lash out to discredit your website for political reasons.
Finally, your competitors may want to attempt to harm or discredit your website and decide to hire a hacker to do it using a DDoS attack.
As you can see, nobody is fully safe from unscrupulous hackers and may be subject to this kind of attack for no particular reason. With that out of the way, let’s take a look at some of the ways you could protect yourself.
Increase Bandwidth
If you can afford to increase bandwidth by upgrading to a better plan with your or another hosting provider, doing so might keep you safe from DDoS attacks. After all, all a DDoS attack does is hog your bandwidth. If your bandwidth capacity surpasses the attacker’s ability to flood your website with requests, the attack will be ineffective. But this does nothing in terms of defending from the attack itself.
Use a CDN
A CDN, or Content Delivery Network, is a network of servers which ensures that the server closest to the request maker gets the request. While primarily designed to reduce latency (improve loading times), using a CDN can have certain benefits with regards to protecting your website from DDoS attacks.
A CDN protects you from a DDoS attack by effectively employing the same tactics as a botnet operator: it distributes the requests among multiple servers, making sure your website doesn’t get overwhelmed. Luckily, there are plenty of CDN providers to choose from.
Use Server-Level DDoS Protection
Some hosting providers offer DDoS protection as part of the package deal you are currently using, meaning you might already have some protection. Others may offer it as an additional paid service, or as part of a different package. Choose a hosting provider willing to protect you from DDoS attacks if one is available, or switch to a package with DDoS protections if you can afford it.
The Rest API is a feature of WordPress which allows plugins and developer tools to access your WordPress data and edit or delete your WordPress content. While it is undeniably useful (essential, even) for normal functioning of WordPress, it represents an avenue of access for hackers. Disabling it will close this avenue off.
There are at least two ways of disabling the JSON Rest API: using a plugin such as Disable WP REST API or by adding code to your functions.php file. Note, though, that flat-out disabling Rest API will prevent you from editing or publishing your posts in case you are using Gutenberg, and may cause issues with certain other plugins or functionalities. Read more on avoiding these issues in our article linked above.
XML-RPC is a system which allows third-party apps to access your website. It is not used very often, but it can present a back door to your website. It is not very difficult to disable XML-RPC for your website: you can do it quickly and easily by locating the .htaccess file and adding the following code to it:
<Files xmlrpc.php> order deny,allow deny from all </Files>
Note that this will prevent you from using the WordPress app on your mobile device from accessing your website (which is used by a small minority of users anyway).
The above actions, as well as certain other useful security practices, do not come in-built with WordPress. You can add these tools to your security toolbox by installing a plugin, and the plugin we recommend is the Defender Security plugin.
After installing and activating the plugin, access its security controls by navigating to Defender from your WordPress dashboard.
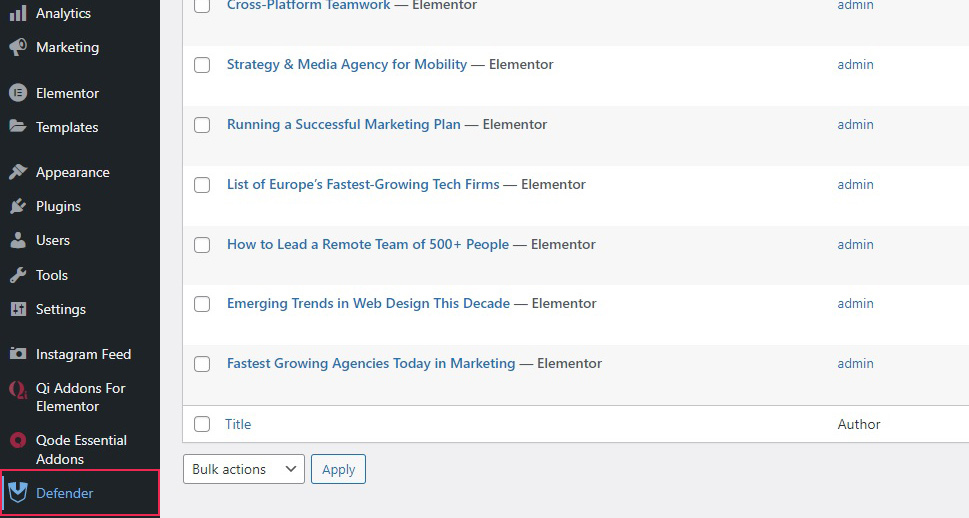
In order to use the plugin, you will need to configure it. Click the Activate & Configure button to begin.
The plugin will go through the configuration process automatically. Once it is done, click the Finish button.
You will then be taken to the plugin’s main screen. There is a lot of different sections here, but your main concern should be the Recommendations section. Click the View All button to access it.
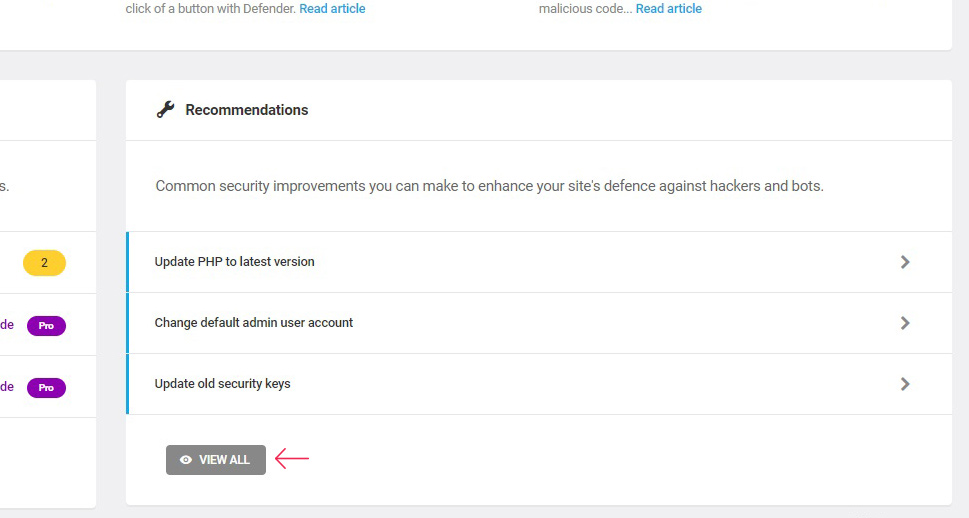
Of the two main vulnerabilities described, you will be able to disable both the Rest API (shown as the Disable the file editor control) and XML-RPC using the Disable XML-RPC control. You can either use the Bulk Actions drop-down menu to accept all recommendations, or go from option to option, clicking each in turn and clicking the requisite button.
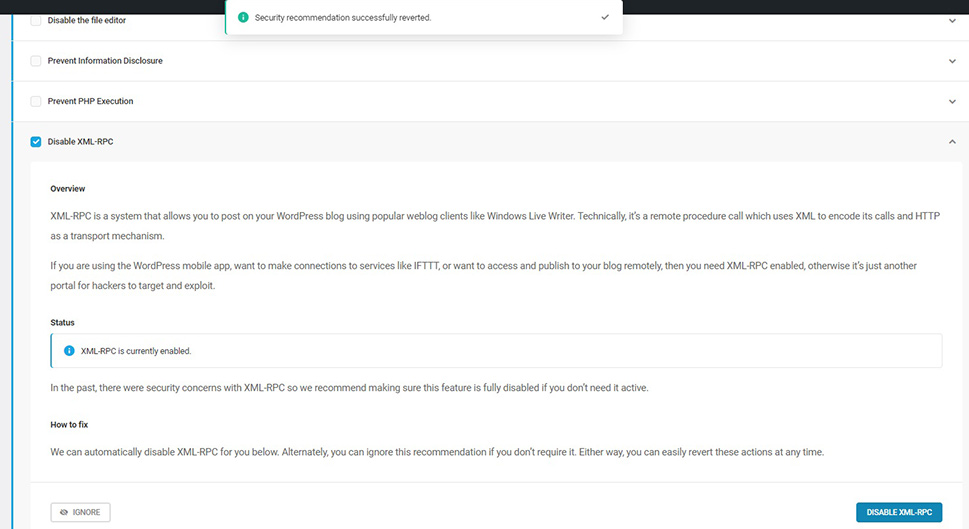
We encourage you to explore the plugin’s other safety features, such as two-factor authentication and login page masking.
You may also prevent DDoS attacks by employing a firewall. There are several good solutions on our list of best firewall plugins for WordPress, and Defender, described above, also has its own firewall feature, though, to fully leverage it, you need to upgrade to the full version of the plugin.
If you don’t want to upgrade the Defender plugin, you can simply select one of the plugins from our list (making sure it has a DoS/DDoS protection feature) and activate it. Some plugins will also allow you to ban specific IP addresses if the owners of those addresses persist in attempting to harm your website using a DDoS attack. If a firewall affects regular website functioning, which some firewalls can do, consult the plugin’s developer.
Blacklist Suspect IP Addresses
This step is connected to the above: persistent hackers who continue to operate repeatedly from the same few IP addresses can be blocked using certain firewall plugins, but there are other ways of blocking suspicious IP addresses from your website. This, however, is a broad topic which merits its own article, and you can (and should) get our take from the article linked in this section.
There is a chance that you have created a vulnerability by installing an unsafe plugin or theme. In that case, you might be able to protect yourself from DDoS attacks and remove the vulnerability if you revert to your website’s latest working version.
There are plenty of ways to manually or automatically back up your website, but they are not the subject of this article. Still, it bears mentioning that reverting to a previous version of the website may remove the vulnerability until such time as you or your staff can fix it..
In Conclusion
As you can see, there is a lot you can do to protect your website from DDoS attacks. Take these simple extra steps to improve your security and make your website continually accessible for your customers and other visitors.